2023. 10. 8. 17:28ㆍAWS
☄️ To-Be Architecture
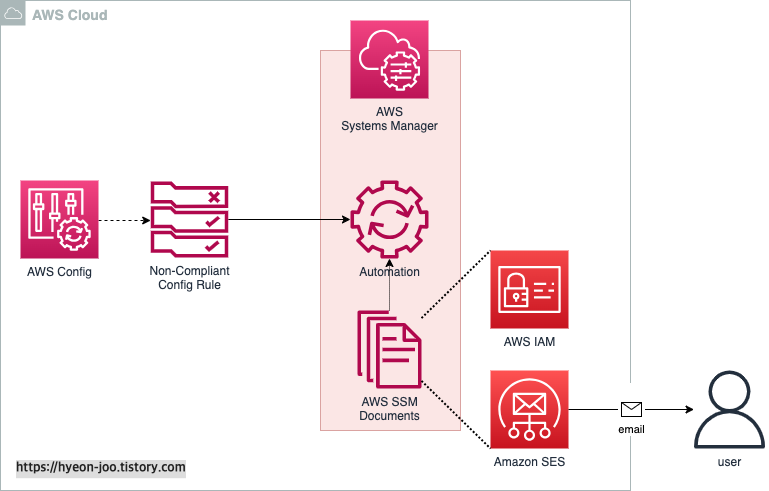
아키텍처의 전체 Flow는 간단하다.
① 일정 기간 사용하지 않은 암호 또는 access key를 가지고 있는 IAM user 추출 ( AWS Config )
② IAM user에 대한 Email 발송 ( AWS SES )
①에 대한 ②의 동작을 자동화하기 위해 AWS Config의 Remediation 기능과 AWS Systems Manager의 Automation을 이용한다.
위 아키텍처를 구성하는 절차는 아래와 같은 순서로 진행하였다.
- AWS Config 규칙 설정
- Amazon SES 사전 설정
- SES로 이메일을 발송하기 위한 AWS SSM Document 스크립트 작성
- 1에서 설정한 Config 규칙에 3의 Document를 연결하는 Config Remediation 설정
1. AWS Config에서 규칙 추가하기

AWS Managed rule 중 iam-user-unused-credentials-check 규칙을 추가하여 AWS IAM(Identity and Access Management) 사용자가 지정된 일 내에 사용되지 않은 암호 또는 활성 액세스 키를 가지고 있는지 확인해 보자.

Evaluation mode
계정에 config rule을 추가할 때, AWS Config가 리소스를 평가할 시기를 지정할 수 있다. Config Rule에 따라 AWS Config는 리소스가 배포되기 전, 또는 리소스가 배포된 후, 또는 두 경우 모두에 리소스 구성을 평가할 수 있다.
- proactive evaluation : 배포되기 전 리소스를 평가
- detective evaluation : 배포된 후 리소스를 평가
trigger type
AWS Config rule이 리소스를 얼마나 자주 평가할지 명시한다. 리로스는 구성 변화가 있을 때 또는 주기적 스케줄을 정해 평가될 수도 있다.
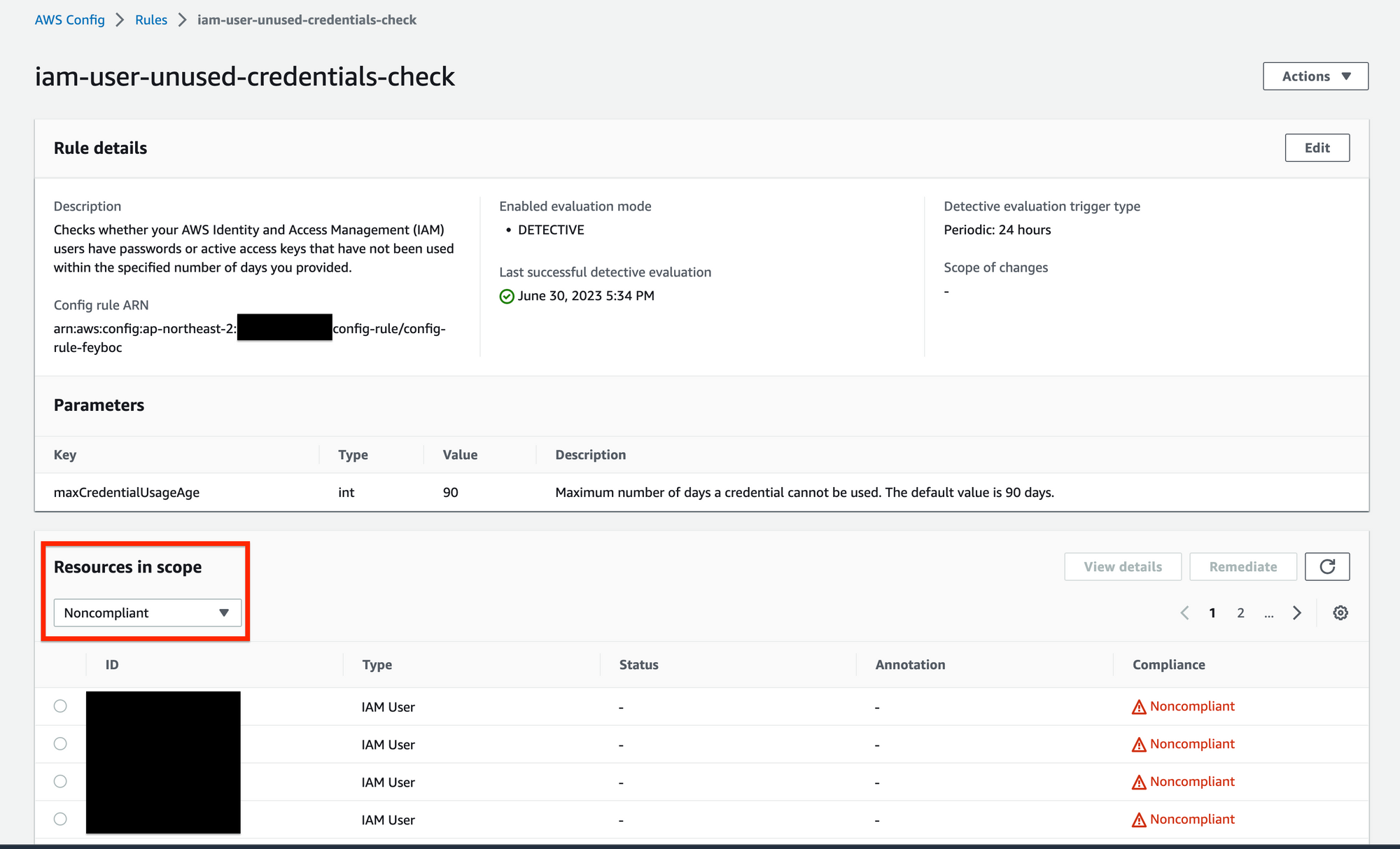
AWS Config Rule을 설정하면 해당 rule을 준수하지 못하는(non-compliant) 리소스를 파악할 수 있다.

Remediate
Config의 기능으로 AWS Config가 Non-Compliant 리소스를 감지하면 AWS Systems Manager Automation 문서를 트리거하여 Non-Compliant 리소스를 원하는 상태로 변경한다. AWS에서 제공하는 Document를 이용할 수도 있고 custom 하게 만든 SSM Document를 이용할 수도 있다.
AWS Config Rule > Action > Manage remediation을 이용하여 해당 rule에 대한 수동 또는 자동 remediation 방법을 설정할 수 있다. 단, service에 연결되지 않은 Config rule에 대해서만 remediation을 설정할 수 있다.
지금은 Remediate에 연결할 Document가 없기 때문에 AWS Systems Manager에서 메일 발송 스크립트 작성 후, 설정한다.
2. Amazon SES 설정하기
2-1. 이메일 주소 확인
Amazon SES를 통해 본인의 이메일 주소에서 이메일을 보내려면 먼저 해당 이메일 주소를 확인하여 이메일 주소의 소유자임을 Amazon SES에 인증해야 한다. 자격증명 생성 후 5분 내에 확인 이메일을 수신해야 한다.

위 그림에서 노란색 칸에 해당하는 링크를 클릭하면 SES console에서 이메일 인증이 verified 되었다는 문구가 뜰 줄 알았는데 계속 시도해도 아래 가이드 문서만 떠서 오류가 발생한 줄 알았다.

링크를 클릭했을 때 저 가이드 문서로 열린다는 게 정말 이상하지만, SES 콘솔에서 해당 이메일이 verified 되었음을 확인할 수 있다.

Send test email을 통해 테스트 이메일을 발송해 볼 수 있다. 테스트 이메일은 인증한 이메일 주소에서 발송된 메일을 첨부파일로 포워딩한 형태로 전송된다.
2-2. SES Sandbox 해제

AWS는 신규 AWS Account를 Amazon SES Sandbox에 배치한다. AWS Account가 Sandbox 상태인 경우, SES의 모든 기능을 사용할 수 있지만 확인된 이메일 주소로만 메일을 보낼 수 있다. AWS Account가 SES Sandbox 상태가 아닌 경우, 수신자의 주소 또는 도메인이 인증되었는지 여부에 관계없이 수신자에게 이메일을 발송할 수 있다. 따라서 sandbox 상태 해제가 필요하다.
📝 Request 원문
- Region : ap-northeast-2
- Use Case: When I receive a request to create an iam user, I will enter the requestor's business email in the user's tag. A notification email will be sent to IAM Users who have not used their credentials for more than 90 days. Therefore, I need a function to send it to an unauthorized mail address.
The email transmission logic using Amazon SES will be included in AWS Systems Manager's document and performed through the automation function. Automation action will be configured to be logged to cloudwatch logs.
The frequency of sending e-mails is currently expected to be 1 to 10 per day. This was calculated by expecting a user who did not access for 90 days among IAM users.
In the body of the mail to be sent, we will make it possible to block the receipt of the mail, including "If you want to block the reception, please give me an email separately" with the administrator's email.
Please move this account out of AWS SES Sandbox.

3. Systems Manager Automation Document 생성
1에서 생성한 AWS Config Rule의 Remediation으로 지정할 AWS Systems Manager Documents를 생성한다.
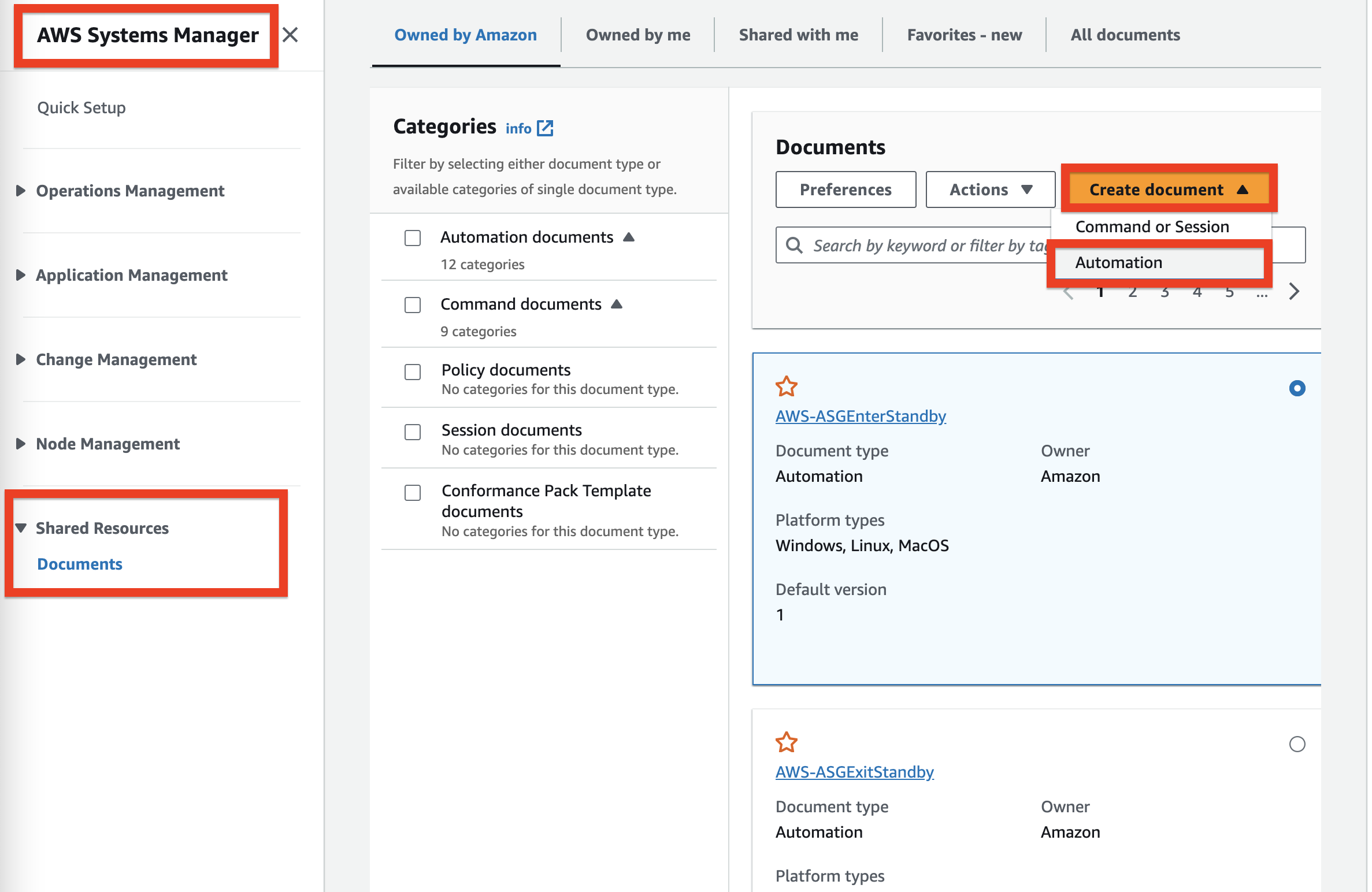
Document 생성 시, 타입은 Automation을 선택한다. Automation은 AWS 리소스에 대한 workflow(유지보수 및 배포 등)를 생성, 관리 및 실행할 수 있는 AWS Systems Manager의 기능이다. SSM Automation은 AWS SSM Document를 활용하여 자동화 워크플로우의 단계와 작업을 정의한다. 반복 작업을 자동화하고 운영 오버헤드를 줄이며 인프라 전반에서 일관된 절차 실행을 보장한다.

💡 참고
AWS는 AWS SSM Document 이름에 접두사로 사용하기 위해 aws, amazon, amzn을 예약했기 때문에 document 생성 시 접두사로 사용할 수 없다.
Input Parameter로 SSM Automation에게 부여할 AutomationAssumeRole, Config Rule에 부합하지 않는 IAM 유저의 ID, 메일 발송을 위한 발신자 이메일과 메일에 표기되는 발신자 이름이 필요하다. 이는 4. Config Remediation 설정에서 입력한다.
Document는 IAM User의 정보를 얻어오는 단계, 그리고 AWS SES를 이용하여 사용자 이메일 주소로 메일을 발송하는 단계의 총 두 단계로 구성하였다.
3-1. (Step 1) GetUserInfo
from time import sleep
import boto3
THROTTLE_PERIOD = 0.05
def get_username(iam_client, iam_user_id):
paginator = iam_client.get_paginator("list_users")
page_iterator = paginator.paginate()
for page in page_iterator:
for user in page["Users"]:
if user["UserId"] == iam_user_id:
return user["UserName"]
sleep(THROTTLE_PERIOD)
def get_user_email_tag(iam_client, iam_username):
tags = iam_client.list_user_tags(UserName=iam_username)
email_tag = list(filter(lambda tag: tag['Key'].lower() == 'email', tags["Tags"]))
return email_tag
def handler(event, context):
iam_client = boto3.client("iam")
iam_user_id = event["IAMUserId"]
iam_username = get_username(iam_client, iam_user_id)
if iam_username is None:
error_message = f"AWS IAM USER ID, {iam_user_id} DOES NOT EXIST."
raise Exception(error_message)
email_tag = get_user_email_tag(iam_client, iam_username)
if len(email_tag) == 1:
return {"UserName":iam_username, "UserEmail": email_tag[0]['Value']}
else:
error_message = f"AWS IAM User {iam_username} DOES NOT HAVE AN EMAIL-RELATED TAGS."
raise Exception(error_message)Boto3 Docs: IAM > Client > list_users (2023.07.02 기준)에 따르면 user의 tag는 리턴되지 않는다. 실제로 resourceID를 통해 list_users로 리턴 받은 user를 출력하면 다음과 같다.
{
"Path": "/",
"UserName": {IAM-USER-NAME},
"UserId": "{IAM-USER-ID}",
"Arn": "arn:aws:iam::{ACCOUNT-ID}:user/{IAM-USER-NAME}",
"CreateDate": "2022-05-31 04:09:05+00:00",
"PasswordLastUsed": "2023-07-02 07:24:36+00:00"
}
따라서 get_username 함수에서 userName을 받고 get_user_email_tag 함수에서 list_user_tags를 이용해 tag를 리턴 받았다. 해당 SSM Automation 문서는 IAM 유저에 "email" 키의 태그가 존재하는 경우에만 메일 발송까지 실행되니 반드시 사전에 IAM 유저의 태그로 email을 입력하는 작업이 필요하다.
3-2. (Step 2) SendEmail
import json
import boto3
import base64
from botocore.exceptions import ClientError
def sendEmail(sender_email, sender_name, user_email, user_name):
CHARSET = "utf-8"
sendername_bytes = sender_name.encode(CHARSET)
sendername_b64 = base64.b64encode(sendername_bytes)
sendername_b64_str = str(sendername_b64)
SENDER_NAME = f"=?{CHARSET}?B?{sendername_b64_str[2:-1]}?="
SENDER = f"{SENDER_NAME} <{sender_email}>"
RECIPIENT = user_email
AWS_REGION = "ap-northeast-2"
SUBJECT = "=====mail subject====="
BODY_TEXT = (f"======body text======")
BODY_HTML = f"""<html>
<head></head>
<body>
<p>AWS IAM 유저 {user_name}에 ??일 동안 사용되지 않은 암호 또는 활성 액세스 키가 있습니다. 조치 바랍니다.</p>
</body>
</html>"""
client = boto3.client('ses',region_name=AWS_REGION)
try:
response = client.send_email(
Destination={
'ToAddresses': [
RECIPIENT,
],
},
Message={
'Body': {
'Html': {
'Charset': CHARSET,
'Data': BODY_HTML,
},
'Text': {
'Charset': CHARSET,
'Data': BODY_TEXT,
},
},
'Subject': {
'Charset': CHARSET,
'Data': SUBJECT,
},
},
Source=SENDER
)
except ClientError as e:
print(e.response['Error']['Message'])
raise e
else:
print("Email sent! Message ID:"),
print(json.dumps(response, indent=2))
def handler(event, context):
sender_email = event["SenderEmail"]
sender_name = event["SenderName"]
user_email = event["UserEmail"]
user_name = event["UserName"]
sendEmail(sender_email, sender_name, user_email, user_name)발신자 이름을 한글로 표기하면 깨지는 현상을 피하기 위해 인코딩 후 문자열을 자르는 단계를 추가하였다. 자세한 내용은 아래 포스팅 참조.
[Amazon SES] SES 메일 발송 시 한글 발신자 이름 깨짐 현상
☄️ 문제 AWS SES API SendEmail를 이용하여 메일을 보내는데 아래와 같이 한글로 입력한 발신자 이름이 정상적으로 출력되지 않았다. 🌎 환경 코드 실행 환경 AWS Systems Automation Document Action : aws:execut
hyeon-joo.tistory.com
3-3. IAM Role 생성
SSM Document가 IAM 유저 정보를 조회하고, SES를 통해 메일을 발송하기 위한 권한이 있는 IAM Role이 필요하다.
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"iam:ListUsers",
"iam:ListUserTags",
"ses:SendEmail",
"ses:SendRawEmail"
],
"Resource": "*",
"Effect": "Allow"
}
]
}
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ssm.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}3-4. Debugging
Automation Document를 수정하면서 Config에서 manage remediate를 통해 테스트를 진행했다. document를 새 버전으로 발행하고 바로 remediate를 수행하면 새 버전을 default 버전으로 지정했음에도 불구하고 새 버전의 document가 반영되지 않는다. 따라서 테스트를 진행할 때는 SSM Document에서 임시 Resource ID를 가져와 Execute automation을 통해 결과를 확인하며 디버깅하는 것이 좋다.
Boto3 Error: botocore.exceptions.NoCredentialsError: Unable to locate credentials
Role 설정이 제대로 되지 않아 발생하는 에러. Automation Document에 assumeRole 값을 확인하자.
4. Config Remediation 설정
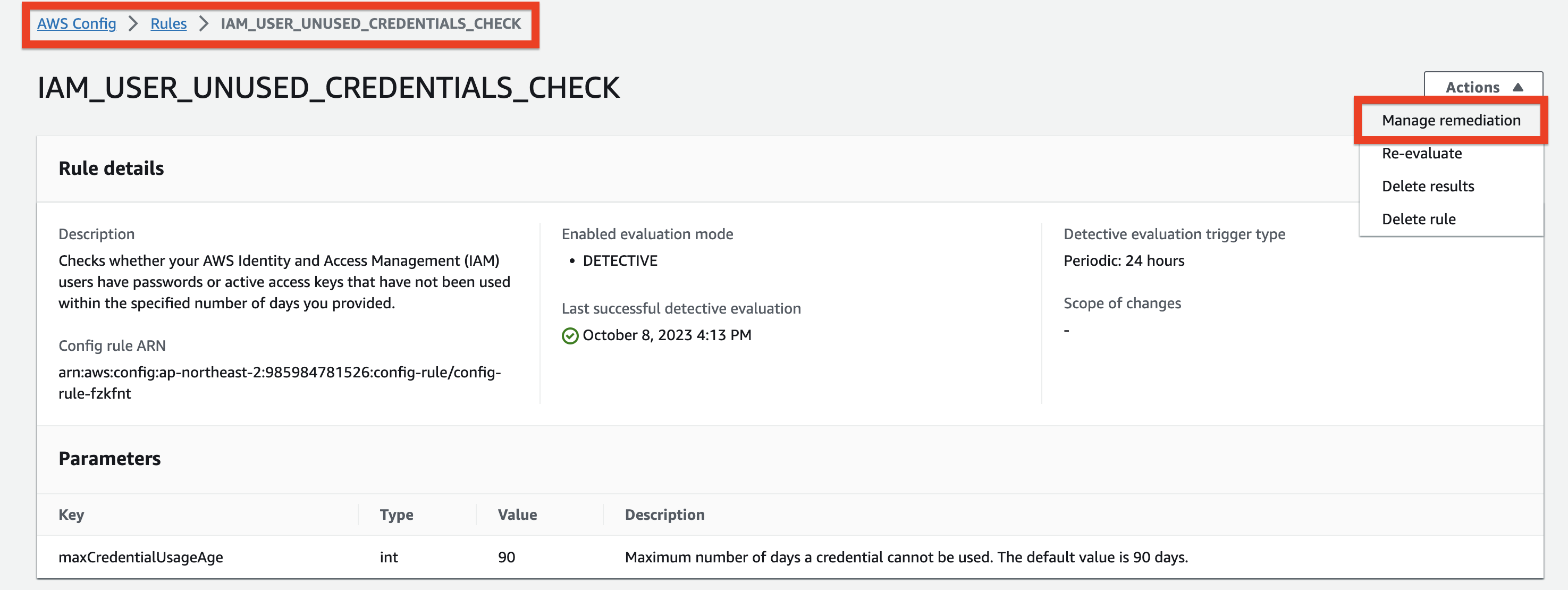
1에서 설정한 Config 규칙에 Config Remediation 설정한다.

Remediation Method에서 Automatic remediation을 선택하고, Remediation action으로는 3에서 생성한 AWS SSM Automation Document를 연결한다.

연결한 SSM Document의 내용에 따라 Resource ID parameter, Parameters를 입력하는 화면이 변경된다. Config Remediation 설정 시 parameters 값을 지정하여 SSM Document의 Input Parameter에 값을 전달한다. Resource ID Parameter를 이용하여 Config rule에 부합하지 않는 리소스의 ID를 전달할 수 있는데 아래 파라미터 중 하나 또는 n/a를 선택하여 아무것도 지정하지 않을 수도 있다. 해당 Config Rule은 일정 기간 미사용하거나 활성화된 액세스 키가 있는 IAM User를 식별하기 때문에 Resource ID는 IAM User의 ID가 되며, 이를 SSM Document의 IAMUserId 파라미터 값으로 전달한다. AutomationAssumeRole에는 3-3에서 생성한 IAM Role의 ARN을 입력하고, SenderName에는 메일 발신자 이름, SenderEmail에는 2-1에서 인증받은 발신자 이메일 주소를 입력한다.
5. 완성

이로써 일정 기간 미사용 IAM 사용자에게 noti 메일 발송 자동화 성공~! 😇
💰 비용 💰
IAM 유저의 수에 따라 다르겠지만 SES는 월 300건 텍스트로 보낸다고 했을 때 1달러 미만으로 비용이 과금될 것으로 예상되고
SSM Automation 예상 비용 또한 1달러 미만으로 발생한다. (2023.07 기준, AWS Cacluator 이용) SES + SSM만 합쳐서는 월 1달러 정도로 저렴하게 자동화 구현에 성공하였다.
🚨 제약 사항 🚨
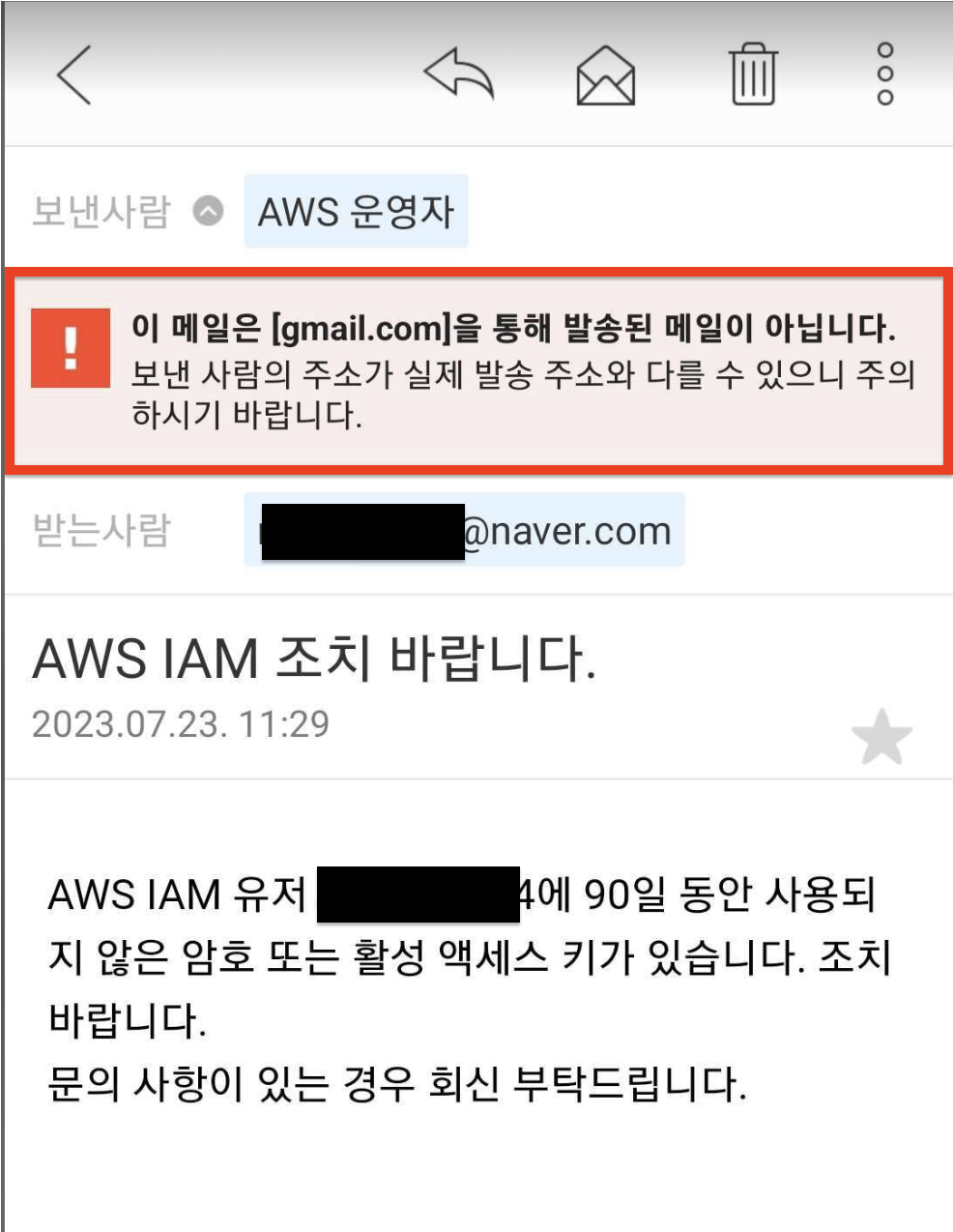
발신자 이메일 주소를 지정하였으나, 실제로 메일을 발송하는 주체는 AWS SES 서비스이기 때문에 원 메일 발송자의 도메인이 @amazonses.com 이 된다. 따라서 메일 수신 측의 정책에 따라 발신자 변조 차단 정책으로 스팸 처리가 될 수 있으며 또는 아래 캡처 화면과 같이 주의 문구가 함께 출력된다.
위에서 설명한 전체 단계를 Cloudformation template 파일로 구성하였습니다.
필요하신 분들은 아래 yaml 파일을 이용해 손쉽게 workflow를 배포하셔도 좋습니다~🍀
🔗 참고 링크
- AWS Docs: Evaluation Mode and Trigger Types for AWS Config Rules
- AWS Docs: Remediating Noncompliant Resources with AWS Config Rules
- AWS Docs: Amazon SES > 이메일 주소 자격 증명 생성
- AWS Docs: AWSConfigRemediation-DeleteIAMUser
- Boto3 Docs: IAM > Client > list_users
- Boto3 Docs: IAM > Client > list_user_tags
- AWS Docs: Moving out of the Amazon SES sandbox
- 기술 블로그(LinkedIn) : AWS IAM Access keys rotation using Lambda function
- AWS Docs: AWS SDK를 사용하여 Amazon SES를 통해 이메일 전송
- AWS Docs: Logging Automation action output with CloudWatch Logs
'AWS' 카테고리의 다른 글
| [AWS Datasync] DataSync를 이용한 S3 간 데이터 복사 (0) | 2024.01.14 |
|---|---|
| [AWS] aws 계정 해지 전, aws-nuke로 간편하게 자원 일괄 삭제하기 (1) | 2023.11.05 |
| [Amazon EventBridge] AWS EventBridge Scheduler를 이용하여 손쉽게 EC2, RDS 중지 및 재시작하기 (0) | 2023.10.01 |
| Multi-account 구조에서 AWS 리소스(EC2, RDS) 자동 시작-중지 스케줄러 구성하기 : Instance Scheduler on AWS (0) | 2023.08.27 |
| [AWS] Amazon Cognito 이용하여 Amazon API Gateway에 인증(Authentication) 추가하기 (0) | 2023.05.08 |